rjohnson11
EVGA Forum Moderator

- Total Posts : 85038
- Reward points : 0
- Joined: 10/5/2004
- Location: Netherlands
- Status: offline
- Ribbons : 86

https://www.kitguru.net/c...-in-windows-and-linux/ Nvidia has unleashed its first security patch of 2019, fixing eight security issues that were present in its GPU Display Driver software. It is advised that both Windows and Linux users update their systems as soon as possible; otherwise they risk possible code execution, denial of service, the dissemination of personal data and perhaps worst of all escalation of privileges. 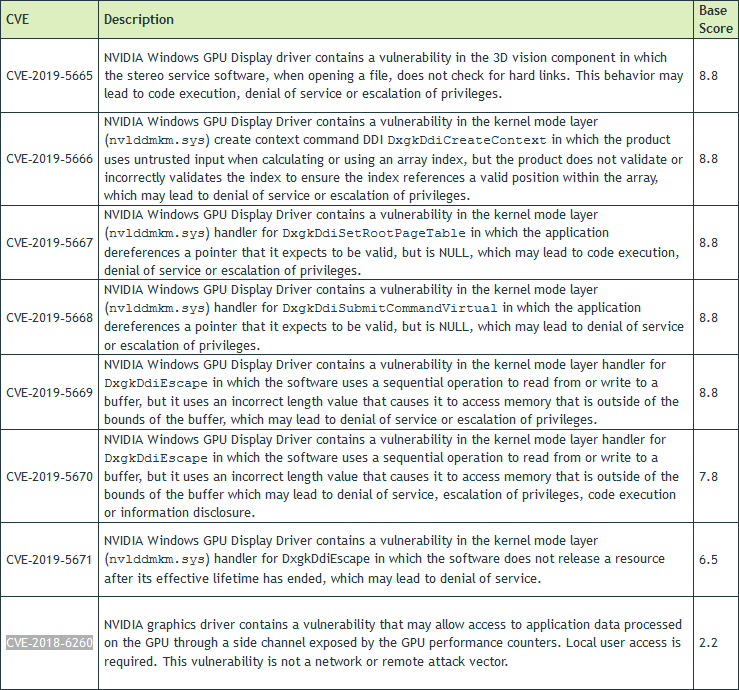
post edited by rjohnson11 - Sunday, March 03, 2019 3:06 PM
|
Cool GTX
EVGA Forum Moderator

- Total Posts : 31353
- Reward points : 0
- Joined: 12/12/2010
- Location: Folding for the Greater Good
- Status: offline
- Ribbons : 123


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Friday, March 01, 2019 4:13 PM
(permalink)
Most important part of that Story:
"Fortunately, the ratings were kept below the “critical” line as none of the software issues could be exploited remotely, requiring local user access."
Learn your way around the EVGA Forums, Rules & limits on new accounts Ultimate Self-Starter Thread For New Members
I am a Volunteer Moderator - not an EVGA employee
Older RIG projects RTX Project Nibbler

When someone does not use reason to reach their conclusion in the first place; you can't use reason to convince them otherwise!
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Friday, March 01, 2019 6:38 PM
(permalink)
Cool GTX
Most important part of that Story:
"Fortunately, the ratings were kept below the “critical” line as none of the software issues could be exploited remotely, requiring local user access."
You can't point out things like that. This is an extreme security issue! Intel and Nvidia are the worst components to have because of their security issues. Doesn't matter if the attack needs to be done locally or that the exploits have never been used in the real world. Hair on fire time!!!! 
|
Cool GTX
EVGA Forum Moderator

- Total Posts : 31353
- Reward points : 0
- Joined: 12/12/2010
- Location: Folding for the Greater Good
- Status: offline
- Ribbons : 123


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Friday, March 01, 2019 6:48 PM
(permalink)
 OK If the Black-hats are in your building you have Much Bigger issues
Learn your way around the EVGA Forums, Rules & limits on new accounts Ultimate Self-Starter Thread For New Members
I am a Volunteer Moderator - not an EVGA employee
Older RIG projects RTX Project Nibbler

When someone does not use reason to reach their conclusion in the first place; you can't use reason to convince them otherwise!
|
GTXJackBauer
Omnipotent Enthusiast
- Total Posts : 10335
- Reward points : 0
- Joined: 4/20/2010
- Location: (EVGA Discount) Associate Code : LMD3DNZM9LGK8GJ
- Status: offline
- Ribbons : 48


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Friday, March 01, 2019 8:20 PM
(permalink)
Use this Associate Code at your checkouts or follow these instructions for Up to 10% OFF on all your EVGA purchases: LMD3DNZM9LGK8GJ
|
Nereus
Captain Goodvibes

- Total Posts : 18192
- Reward points : 0
- Joined: 4/10/2009
- Location: Brooklyn, NYC.
- Status: offline
- Ribbons : 58


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Friday, March 01, 2019 11:45 PM
(permalink)
kram36
You can't point out things like that.
This is an extreme security issue!
Intel and Nvidia are the worst components to have because of their security issues. Doesn't matter if the attack needs to be done locally or that the exploits have never been used in the real world.
Hair on fire time!!!!

LMAO!!!
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Saturday, March 02, 2019 1:59 AM
(permalink)
kram36
[repetitive sarcasm]
Intel and Nvidia are the worst components to have because of their security issues. Doesn't matter if the attack needs to be done locally or that the exploits have never been used in the real world.
[/repetitive sarcasm]
To be fair, the Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code. Thankfully, the known holes were patched. Comparing the Intel prediction exploit to these NVIDIA exploits, at least at face value (based on NVIDIA's word), is a laugh.
post edited by ty_ger07 - Saturday, March 02, 2019 4:08 AM
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Saturday, March 02, 2019 4:29 AM
(permalink)
ty_ger07
kram36
Intel and Nvidia are the worst components to have because of their security issues. Doesn't matter if the attack needs to be done locally or that the exploits have never been used in the real world.
To be fair, the Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code. Thankfully, the known holes were patched.
Comparing the Intel prediction exploit to these NVIDIA exploits, at least at face value (based on NVIDIA's word), is a laugh.
Remember this? https://www.theregister.co.uk/2018/07/17/spectre_protectors/ Apvrille's work backs up what we've heard from other researchers: so far, Spectre exploitation is theoretical, with no exploits in the wild. She wrote that while there was a flurry of “Spectre exploit” stories based on AV-Test sample collection, it turned out that all of the reported samples were proofs-of-concept rather than genuine malware.
post edited by kram36 - Saturday, March 02, 2019 6:20 AM
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Saturday, March 02, 2019 6:27 PM
(permalink)
Remember this?
To be fair, the Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code. Thankfully, the known holes were patched.
I don't care if no one has provided evidence of the vulnerability being used in the wild. The demonstrated scope of the vulnerability was terrifying on its own. Thankfully it was quickly patched. What I want to know is why are you comparing the Intel prediction exploit to the above NVIDIA vulnerabilities? Like, what are you doing bringing up old unrelated opinions?
post edited by ty_ger07 - Saturday, March 02, 2019 6:33 PM
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Saturday, March 02, 2019 7:40 PM
(permalink)
ty_ger07
Remember this?
Blah, blah, I really don't understand how hard these exploits are to use, but blah!!! Thankfully, the known holes were patched.
I don't care if no one has provided evidence of the vulnerability being used in the wild. The demonstrated scope of the vulnerability was terrifying on its own. Thankfully it was quickly patched. What I want to know is why are you comparing the Intel prediction exploit to the above NVIDIA vulnerabilities? Like, what are you doing bringing up old unrelated opinions?
You don't care if these exploits have never seen a day of light in the real world. While at the same time you know they are patched and you're terrified of them and act like it's the end of the world. You're the boy crying wolf. I brought it up as rjohnson11 just loves to toss out any bad information on Intel and Nvidia, such as this thread and Cool GTX put the fire out on this by actually reading the article and not going on a fear rampage.
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 03, 2019 2:52 PM
(permalink)
You don't care if these exploits have never seen a day of light in the real world. They did see the light of day in the real world. They were demonstrated and the results were terrifying. Just because there is no proof that they were used against someone in the real world doesn't mean that they were never executed in the real world. Demonstration = real world. It was terrifying. That's why there was so much news about it. Again, Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code.
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
Nereus
Captain Goodvibes

- Total Posts : 18192
- Reward points : 0
- Joined: 4/10/2009
- Location: Brooklyn, NYC.
- Status: offline
- Ribbons : 58


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 03, 2019 2:56 PM
(permalink)
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 03, 2019 4:31 PM
(permalink)
ty_ger07
You don't care if these exploits have never seen a day of light in the real world.
They did see the light of day in the real world. They were demonstrated and the results were terrifying. Just because there is no proof that they were used against someone in the real world doesn't mean that they were never executed in the real world. Demonstration = real world. It was terrifying. That's why there was so much news about it. Again, Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code.
You really need to educate yourself. A remote attack is extremely complex and you're making it out like this is an easy attack to execute for the attacker. https://duo.com/decipher/netspectre-highlights-new-ways-exploit-speculative-execution Each network hop between switches adds entropy to the latency of the overall request, Davidov said. Trying to execute the attack over the Internet might make it impossible to execute Current attacks are very impractical and would likely not apply well in real-world scenarios, said Mikhail Davidov, senior security researcher at Duo Security. Threat actors have access to much easier tools to compromise victims—they won’t need to deal with the complexity and uncertainty of a network-based Spectre attack. Spectre’s countermeasures are effective for NetSpectre. If the system is fully patched against Spectre, it also blocks NetSpectre attacks. There is no known malware exploiting NetSpecture, or other Spectre and Meltdown variants.
post edited by kram36 - Sunday, March 03, 2019 4:38 PM
|
Sajin
EVGA Forum Moderator

- Total Posts : 49227
- Reward points : 0
- Joined: 6/8/2010
- Location: Texas, USA.
- Status: offline
- Ribbons : 199


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 03, 2019 7:28 PM
(permalink)
kram36
Cool GTX
Most important part of that Story:
"Fortunately, the ratings were kept below the “critical” line as none of the software issues could be exploited remotely, requiring local user access."
You can't point out things like that.
This is an extreme security issue!
Intel and Nvidia are the worst components to have because of their security issues. Doesn't matter if the attack needs to be done locally or that the exploits have never been used in the real world.
Hair on fire time!!!!


|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 1:42 AM
(permalink)
You really need to educate yourself. A remote attack is extremely complex and you're making it out like this is an easy attack to execute for the attacker.
https://duo.com/decipher/...-speculative-execution
Each network hop between switches adds entropy to the latency of the overall request, Davidov said. Trying to execute the attack over the Internet might make it impossible to execute
Not impossible. Far from it. Like I said, it was even demonstrated. Worked fine. Before the browsers and javascript engine was patched, it was doable with javascript. No, no; not java. Javascript. ...The thing your browser is using right now to view this website. Javascript runs client-side and requires no network hops. You make a javascript application to exploit the speculation vulnerability, place it inside a website and find a way to promote traffic to your website, the javascript runs client-side for any user who visits your website and uses no further internet connection, and when it finds what it is asked to find, that's the only time it uses the network to send the information back to the attacker. Demonstrated. Worked. Your basing your opinion on current opinions after everything was patched. Before it was patched, it was terrifying. Therefore, newsworthy.
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 2:23 AM
(permalink)
ty_ger07
You really need to educate yourself. A remote attack is extremely complex and you're making it out like this is an easy attack to execute for the attacker.
https://duo.com/decipher/...-speculative-execution
Each network hop between switches adds entropy to the latency of the overall request, Davidov said. Trying to execute the attack over the Internet might make it impossible to execute
Not impossible. Far from it. Like I said, it was even demonstrated. Worked fine. Before the browsers and javascript engine was patched, it was doable with javascript. No, no; not java. Javascript. ...The thing your browser is using right now to view this website. Javascript runs client-side and requires no network hops.
You make a javascript application to exploit the speculation vulnerability, place it inside a website and find a way to promote traffic to your website, the javascript runs client-side for any user who visits your website and uses no further internet connection, and when it finds what it is asked to find, that's the only time it uses the network to send the information back to the attacker. Demonstrated. Worked.
Your basing your opinion on current opinions after everything was patched. Before it was patched, it was terrifying. Therefore, newsworthy.
Actually no, it wasn't terrifying. With most vulnerabilities, the fact that it can be exploited remotely would move the flaw up higher on the critical scale. That isn’t the case with NetSpectre, because it is an extremely slow attack, leaking 15 bits per hour, or 60 bits an hour via an AVX-based covert channel. It could take days to find and gather secrets such as encryption keys or authentication tokens.
Current attacks are very impractical and would likely not apply well in real-world scenarios,” said Mikhail Davidov, senior security researcher at Duo Security. This type of exploit being used over the internet makes it pretty much worthless as said in the article. The precise timing and constant measurement required for NetSpectre makes it likely that noisy network environments would hamper execution. The research team’s proof-of-concept doesn’t reflect real-world situations, as the servers weren’t dealing with real traffic. The attack code was on a purpose-built application with only a single use. If the application had been dealing with a “real load” and not ideal network conditions, it would have slowed the attack down even further, Davidov said.
Each network hop between switches adds entropy to the latency of the overall request,” Davidov said. Trying to execute the attack over the Internet “might make it impossible to execute. Did you even read the article?
post edited by kram36 - Monday, March 04, 2019 2:31 AM
|
MasterMiner
SSC Member
- Total Posts : 713
- Reward points : 0
- Joined: 1/26/2018
- Status: offline
- Ribbons : 2


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 2:51 AM
(permalink)
I do hate agreeing with kram, on anything... but on this he’s right. The complexity of a completely remote attack without having a previously compromised system by some sort of internal operation / malware click, social engineering is incredibly difficult. It’s the stuff of nation-state actors using means and methods no normal human would have the resources to replicate. Social engineering, getting someone on the inside to do something dumb or who you can compromise personally is far easier. [edit] I would point out that nation-states indeed *do* have this capability, particularly the biggies (Russia, China, Us, Israel, maybe France, UK). But any such attack, particularly on infrastructure, would be attributable and a declaration of war.
post edited by MasterMiner - Monday, March 04, 2019 3:03 AM
I used to mine. Now I compute.
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 3:24 AM
(permalink)
MasterMiner
I would point out that nation-states indeed *do* have this capability, particularly the biggies (Russia, China, Us, Israel, maybe France, UK). But any such attack, particularly on infrastructure, would be attributable and a declaration of war.
I don't think the tools they have use the cpu speculative execution exploit. I could be wrong though.
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 1:07 PM
(permalink)
MasterMiner
I do hate agreeing with kram, on anything... but on this he’s right.
The complexity of a completely remote attack without having a previously compromised system by some sort of internal operation / malware click, social engineering is incredibly difficult.
Unpatched, it required no previous compromises. I don't know why you made that statement. Like I said, any operating system install was exploitable by javascript in any web browser on any malicious website. Mac OS, Linux, Windows, all. No sandboxes stopped it. What is he talking about? Network load? NetSpectre? Why is he changing the subject? I am not talking about NetSpectre. I am talking about simple Meltdown in its original unpatched form. Javascript has virtually no network load. It is a client-side application. Did I even read the article? Ummm... did he even link relevant information? No. Just search "spectre javascript" and you will find all sorts of examples and articles from before it was patched. Not NetSpectre. Not something which requires high network precision or creates a lot of network traffic. Of course it could also be exploited locally by downloading a bad program. But it is often harder to trick someone to do that. So, you put the malicious code in a website, and it does the exact same thing (automatically downloads the javascript and runs locally) without the user being aware or as cautious. And since the javascript was already trusted by your computer and you told the computer that you trusted the website by choosing to visit it, your computer doesn't think it is suspicious to send some data back to that website (once the javascript finds whatever it is programmed to find). Javascript runs client-side applications and asynchronously sends and receives information every day. It wouodn't be an abnormal thing. There is information asynchronously sent and received and calculated client-side by viewing this website.
post edited by ty_ger07 - Monday, March 04, 2019 1:21 PM
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 3:03 PM
(permalink)
ty_ger07
MasterMiner
I do hate agreeing with kram, on anything... but on this he’s right.
The complexity of a completely remote attack without having a previously compromised system by some sort of internal operation / malware click, social engineering is incredibly difficult.
Unpatched, it required no previous compromises. I don't know why you made that statement. Like I said, any operating system install was exploitable by javascript in any web browser on any malicious website. Mac OS, Linux, Windows, all. No sandboxes stopped it. Because what I posted is correct. ty_ger07
What is he talking about? Network load? NetSpectre? Why is he changing the subject? I am not talking about NetSpectre. I am talking about simple Meltdown in its original unpatched form. Javascript has virtually no network load. It is a client-side application. Did I even read the article? Ummm... did he even link relevant information? No. I never changed the subject and the information is very relevant, but you wouldn't know that since you didn't read the article. I thought you considered this security issue to be terrifying, but you won't read an article on it? ty_ger07
Just search "spectre javascript" and you will find all sorts of examples and articles from before it was patched. Not NetSpectre. Not something which requires high network precision or creates a lot of network traffic.
I thought you wanted to change the subject over to Metldown? But you're saying to search "spectre javascript"? How do you know if NetSpectre is not javascript based if you didn't read the article? This study shows that javascript will have the time issue with spectre. Even though all browsers have now addressed this issue, but for someone that is running a year old browser and never updated, it's still falls into the issue of needing enough time in order for the spectre exploit operations to get the data and transfer it. https://blog.renditioninfosec.com/files/Rendition_Infosec_Meltdown_and_Spectre_20180108.pdf#page=26 Tests indicate that the number of operations required for Spectre may be infeasible in JavaScript unless a user stays on a page for a LONG time.
post edited by kram36 - Monday, March 04, 2019 7:15 PM
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 7:16 PM
(permalink)
How do you know if NetSpectre is not javascript based if you didn't read the article? Because the Javascript approach does not create high network load. It is a client-side application just like any other program you download and execute. Therefore it could not possibly be relevant. I didn't have to read the article to know that your comment and quote was not relevant. Javascript is a client-side application framework which is included with any modern browser in any modern operating system and is required by the majority of modern websites and is therefore by default automatically trusted and executed without any user prompt or notification.
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 04, 2019 7:25 PM
(permalink)
ty_ger07
How do you know if NetSpectre is not javascript based if you didn't read the article?
Because the Javascript approach does not create high network load. It is a client-side application just like any other program you download and execute. Therefore it could not possibly be relevant. I didn't have to read the article to know that your comment and quote was not relevant.
Javascript is a client-side application framework which is included with any modern browser in any modern operating system and is required by the majority of modern websites and is therefore by default automatically trusted and executed without any user prompt or notification.
You replied right as I was adding more info to my post. It's not just the network load, it's also the time it takes for the spectre exploit operations. This study shows that javascript will have the time issue with spectre. Even though all browsers have now addressed this issue, but for someone that is running a year old browser and never updated, it's still falls into the issue of needing enough time in order for the spectre exploit operations to get the data and transfer it. https://blog.renditioninfosec.com/files/Rendition_Infosec_Meltdown_and_Spectre_20180108.pdf#page=26 Tests indicate that the number of operations required for Spectre may be infeasible in JavaScript unless a user stays on a page for a LONG time.
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Saturday, March 09, 2019 3:35 PM
(permalink)
All of the speculative exploits take time. If you know where the data your after is located, it is fast. If you have to do a lot of searching, it is slow. Using a website-based attack, choosing the proper type of website would be crucial in ensuring the attacker's success rate. If they included the code inside a audio or video streaming website, or a stock or news ticker/graph website, the success rate would be much higher than a blog, for example. As you finally realized, it was all possible; and that level of compromise is extremely rare. I am glad that you now agree that:
To be fair, the Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code. Thankfully, the known holes were patched.
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
veganfanatic
CLASSIFIED Member
- Total Posts : 2134
- Reward points : 0
- Joined: 6/21/2015
- Status: offline
- Ribbons : 1


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Saturday, March 09, 2019 8:03 PM
(permalink)
having read that article they are behind with 419.17 when 419.35 is been out for several days now
lets try to stay focused on today, not last months headaches
  Corsair Obsidian 750D Airflow Edition + Corsair AX1600i PSUMy desktop uses the ThinkVision 31.5 inch P32p-20 Monitor.My sound system is the Edifier B1700BT Corsair Obsidian 750D Airflow Edition + Corsair AX1600i PSUMy desktop uses the ThinkVision 31.5 inch P32p-20 Monitor.My sound system is the Edifier B1700BT
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 10, 2019 3:33 PM
(permalink)
ty_ger07
All of the speculative exploits take time. If you know where the data your after is located, it is fast. If you have to do a lot of searching, it is slow. Using a website-based attack, choosing the proper type of website would be crucial in ensuring the attacker's success rate. If they included the code inside a audio or video streaming website, or a stock or news ticker/graph website, the success rate would be much higher than a blog, for example.
As you finally realized, it was all possible; and that level of compromise is extremely rare. I am glad that you now agree that:
To be fair, the Intel prediction exploit didn't require any special privileges, didn't require any additional malicious software or previous system compromises, could be exploited right after a fresh operating system install with no special software required, could be exploited remotely without any special access to the system, could read absolutely anything out of any part of system memory regardless of any existing operating system, software, or hardware attempts at protecting memory addresses, and was functionally demonstrated both locally and remotely using example code. Thankfully, the known holes were patched.
It took you 5 days to come back with this load of garbage? It works faster when you know where the data you're after is located? What the hell are you talking about? You have zero clue what data is on any computer, you have zero clue of where the data is being stored or if it's even stored in the cache at all. This is why it takes so long. This is the most illogical post you have made on this speculative execution exploit, I can't even believe you typed this out and thought it was a smart idea to post on the forums. As for for you saying I am finally agreeing that these exploits are real, I never said they were not real, I said they have never been used in the real world to attack anyone. They are difficult to execute, they take a long time and hackers have easier tools to use to get what they want.
post edited by kram36 - Sunday, March 10, 2019 3:56 PM
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 4/11/2008
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 10, 2019 4:20 PM
(permalink)
You have heard of reserved memory addresses before, right? I feel like I am arguing with a loud rock. Long, slow? Yeah, sometimes. Fast if accessing a known location. Slow if searching. But people made a lot of money from monero mining javascript, so you know that there are groups of people who will use certain types of websites conducive for long javascript sessions. Never used? Well, I think that is impossible to prove. We cannot prove that it was used. But can we prove that it was never used? Of course not. But we can prove that it was demonstrated and functional. Easier tools for hackers? Maybe. But those easier tools are often not powerful and often require that the user do dumb things to become compromised. This approach was much more powerful, had enormous access, and didn't require that the user do anything objectively dumb to become compromised. Visit the wrong website and potentially have any portion of your system memory compromised? That's bad. veganfanatic
having read that article they are behind with 419.17 when 419.35 is been out for several days now
lets try to stay focused on today, not last months headaches
I agree. But he has been very loud about this for months. He brought it up again, and I can't quietly stand by as he spouts a bunch of loud nonsense.
post edited by ty_ger07 - Sunday, March 10, 2019 4:23 PM
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
atfrico
Omnipotent Enthusiast
- Total Posts : 9738
- Reward points : 0
- Joined: 5/20/2008
- Location: <--Dip, Dip, Potato Chip!-->
- Status: offline
- Ribbons : 25


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 10, 2019 9:40 PM
(permalink)
veganfanatic
having read that article they are behind with 419.17 when 419.35 is been out for several days now
lets try to stay focused on today, not last months headaches
I am glad the new drivers came up....i'd been having crashes lately from the 2 previous drivers before this one. Just be on the look up. I believe Nvidia is sabotaging consumers with faulty drivers.
T hose who abuse power, are nothing but scumbags! The challenge of power is how to use it and not abuse it. The abuse of power that seems to create the most unhappiness is when a person uses personal power to get ahead without regards to the welfare of others, people are obsessed with it. You can take a nice person and turn them into a slob, into an insane being, craving power, destroying anything that stands in their way. Affiliate Code: 3T15O1S07G
|
kram36
The Destroyer

- Total Posts : 20362
- Reward points : 0
- Joined: 10/28/2009
- Location: United States
- Status: offline
- Ribbons : 72

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 10, 2019 10:58 PM
(permalink)
ty_ger07
You have heard of reserved memory addresses before, right? I feel like I am arguing with a loud rock.
Yes I have and apparently you have zero clue how the reserved memory address is stored. I feel like I am arguing with a loud rock. ty_ger07
Long, slow? Yeah, sometimes.
No, it's every single time. There is no speeding it up. ty_ger07
Never used? Well, I think that is impossible to prove. We cannot prove that it was used. But can we prove that it was never used? Of course not. But we can prove that it was demonstrated and functional.
If you don't think we would know about these exploits actually used with success in the real world and we have not heard about it, you're out of your mind. Most systems are patched, at least systems that are worth patching have been patched. ty_ger07
veganfanatic
having read that article they are behind with 419.17 when 419.35 is been out for several days now
lets try to stay focused on today, not last months headaches
I agree. But he has been very loud about this for months. He brought it up again, and I can't quietly stand by as he spouts a bunch of loud nonsense.
You have zero clue about how these exploits work. You're the one that has been very loud about this for months and I can't quietly stand by as you spouts a bunch of loud nonsense.
post edited by kram36 - Sunday, March 10, 2019 11:02 PM
|
Nereus
Captain Goodvibes

- Total Posts : 18192
- Reward points : 0
- Joined: 4/10/2009
- Location: Brooklyn, NYC.
- Status: offline
- Ribbons : 58


Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Sunday, March 10, 2019 11:46 PM
(permalink)
|
bill1024
Omnipotent Enthusiast
- Total Posts : 11703
- Reward points : 0
- Joined: 10/18/2008
- Status: offline
- Ribbons : 65

Re: Nvidia’s latest GPU Display Driver patches 8 security issues in Windows and Linux
Monday, March 11, 2019 0:04 PM
(permalink)
Nereus


Where the heck is that like button when you need it?
Life is too short to carry a cheap pocket knife 
|