rjohnson11
EVGA Forum Moderator

- Total Posts : 85038
- Reward points : 0
- Joined: 2004/10/05 12:44:35
- Location: Netherlands
- Status: offline
- Ribbons : 86


Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation | TechPowerUp Over the past few generations, Razer has automated the download and installation of the Razer Synapse software by having it start the first time to plug in a Razer peripheral on your computer (mouse, keyboard, USB headset, etc.). This may be well-intentioned, but comes with a glaring security flaw, according to a LifeHacker report citing a security discovery by @j0nh4t on Twitter. Apparently, plugging in a Razer peripheral causes the Razer Synapse installer to prompt download and installation using a privileged Windows process (using Windows Update). Once you download and run the installer, you can choose a custom installation folder for the application. This spawns a Windows Explorer dialog that is privileged and can access folders regular users probably don't have access to, as per an organization's group policy. Once in this dialog, you can simply shift+right-click on a folder, and click on "open PowerShell window here," to spawn a privileged PowerShell at that location, and knock yourself out with whatever it is you want to do to the machine. Visit the source link below for a video demo on how this hack works. This is a really bad security flaw that needs to be fixed ASAP in my opinion. 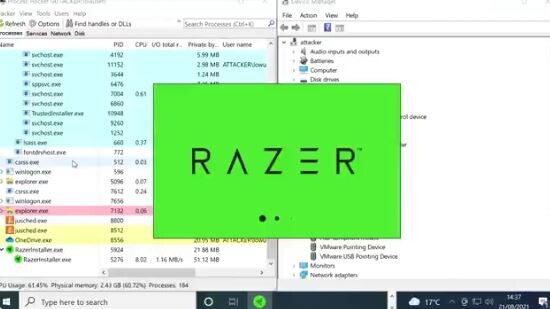
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 2008/04/10 23:48:15
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation
2021/08/24 10:12:53
(permalink)
I don't understand exactly how this happens. Like, what gives that software authority to open stuff with privileged access? If so, why can't anyone just create a program which does the same thing? This means that Razer has access to something that was vetted and signed by Microsoft which allowed their program to gain that privilege level? If so, who is at fault?
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
Flint 1760
Omnipotent Enthusiast
- Total Posts : 8149
- Reward points : 0
- Joined: 2009/04/26 15:44:26
- Status: offline
- Ribbons : 45

Re: Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation
2021/08/24 12:20:17
(permalink)
The automatic installation and download of the utility when you plug in the mouse and allowing access is Razer's fault. An install utility for a mouse should never have that level of privilege. An individual has to physically open Power Shell after the install on the target computer, which for the home user is not a big problem. For corporate systems it is possibly a really big problem.
I do not like automatic downloads or updates as I want the choice. I understand Razer is working on a patch.
In the meantime when you go into work, you will be searched to see if you have a Razer mouse in your pocket.
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 2008/04/10 23:48:15
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation
2021/08/24 14:41:10
(permalink)
Flint 1760
The automatic installation and download of the utility when you plug in the mouse and allowing access is Razer's fault. An install utility for a mouse should never have that level of privilege.
What is the mechanism that allows Razer's application to even escalate itself to that level of privilege? That's the heart of my question. A normal user shouldn't be able to write an application that can do that, right? Otherwise, every hacker would. So, there is a mechanism being utilized, and my question is 'what is the mechanism?". A driver signature?
post edited by ty_ger07 - 2021/08/24 14:44:12
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
Flint 1760
Omnipotent Enthusiast
- Total Posts : 8149
- Reward points : 0
- Joined: 2009/04/26 15:44:26
- Status: offline
- Ribbons : 45

Re: Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation
2021/08/24 15:40:28
(permalink)
Here is some further information and based on it, I would say Razer’s installer is to blame. “A security researcher named Jon Hat recently revealed that you could gain SYSTEM access on a PC by plugging in a Razer gaming mouse or dongle (via Neowin). If you have local access to a machine, plugging in a Razer device installs RazerInstaller.exe, which runs with SYSTEM privileges. It also allows someone to open Windows PowerShell and the File Explorer with elevated privileges. With this exploit, someone could install harmful software onto a computer. Because of the nature of the vulnerability, a person requires physical access to a PC to exploit it. This makes it less dangerous than a vulnerability that can be exploited remotely, but it still leaves a security risk. While separate, this Razer-related vulnerability has some characteristics in common with the PrintNightmare vulnerabilities on Windows 10. Both types of vulnerabilities rely on someone installing an item on a local account and gaining SYSTEM privileges despite not being an admin on a computer. Hat explains that he reported the vulnerability to Razer but did not initially hear back from the company. Following this, Hat shared the vulnerability publicly. Since, Razer has responded to Hat, explaining that it is working on a fix.” Source: Windows Central
|
ty_ger07
Insert Custom Title Here

- Total Posts : 16602
- Reward points : 0
- Joined: 2008/04/10 23:48:15
- Location: traveler
- Status: offline
- Ribbons : 271


Re: Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation
2021/08/24 21:15:00
(permalink)
Is anyone able to answer my question? An application is not supposed to be able to elevate its privileges higher than the user who initiated it, right? So what allowed this Razer application to do so? Is this a Windows Update exploit discovered by Razer? Or is it the driver signature which allowed it to open an application via Windows Update with elevated privileges? What allowed the RazerInstaller to open with system privileges even if the user wasn't at that privilege level?
post edited by ty_ger07 - 2021/08/25 04:45:43
ASRock Z77 • Intel Core i7 3770K • EVGA GTX 1080 • Samsung 850 Pro • Seasonic PRIME 600W Titanium
|
a213m
SSC Member
- Total Posts : 886
- Reward points : 0
- Joined: 2006/02/08 11:10:24
- Location: 🇨🇦
- Status: offline
- Ribbons : 20


Re: Hack a PC? Plug in a Razer Mouse with Automatic Synapse Installation
2021/08/25 00:00:08
(permalink)
Not really a vulnerability. 1 - Requires preinstalled software; 2 - requires physical access to a PC.
My free and open source SDR-DDR5 SPD reader/writer with write protection capabilities New: 13900K, Z790 HERO, 2x32GB 6800C32, 4090, 2TB SN850, AX1600iOld: 10980XE, X299SE2, 8x8GB 4000C15, 4090, 2TB SN850, AX1600i
|